Network anomaly detection system
Tackle network issues & security threats
Advantage at every stage of compromise
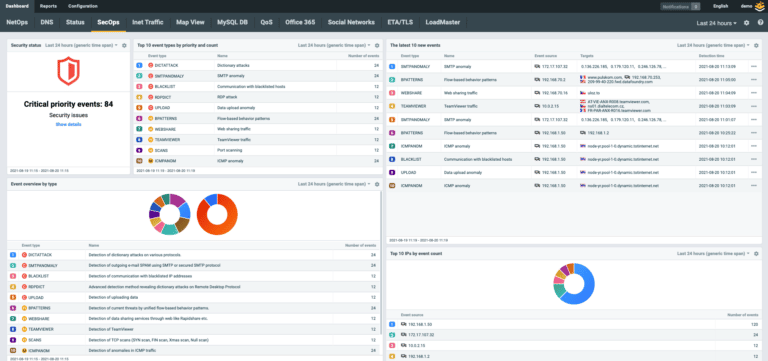
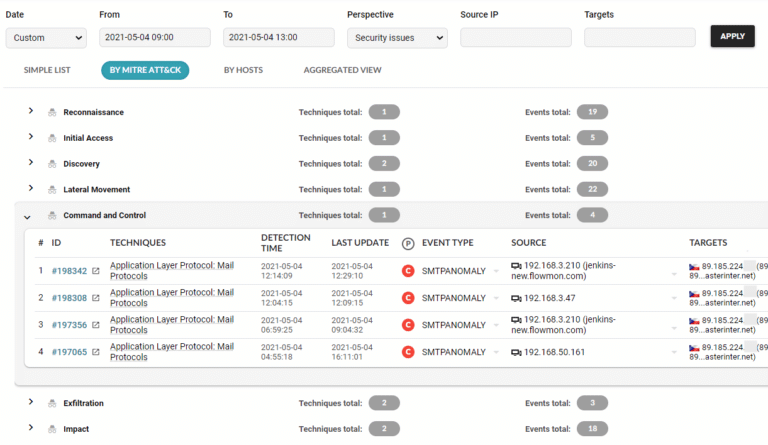
Flowmon ADS adds the network-centric layer of defense to your security matrix (see SOC Visibility Triad) to detect the slightest network anomalies that indicate the activity of unknown and insider threats undetectable by perimeter and endpoint security. Context-rich incident visualization in the MITRE ATT&CK® framework keeps you briefed on the scope, severity and future development of the breach.
Automated detection and response (NDR)
Threats are detected early, instantly and automatically thanks to 40+ AI-based methods and 200+ algorithms. Reveal unknown threats, malware, ransomware, Windows DNS SIGRed exploitation, Trojan attacks or threats hidden in encrypted traffic. The ADS can be integrated with network access control, authentication, firewall and other tools for immediate incident response.
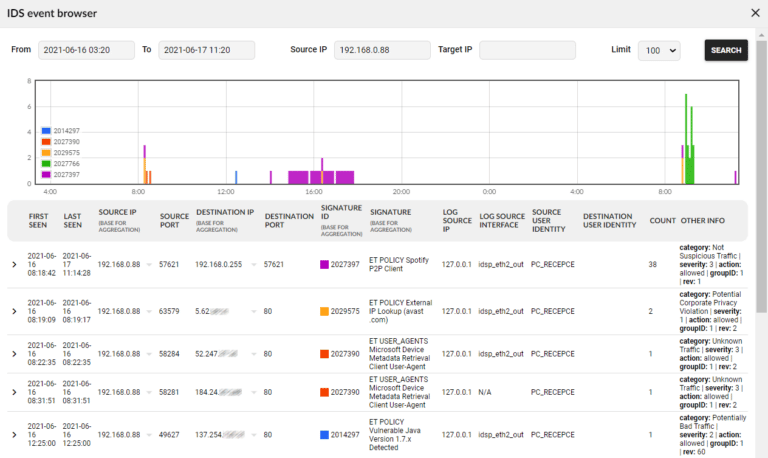
Leverage Flowmon IDS Probe powered by Suricata
Flowmon ADS includes a built-in IDS collector that receives events from Flowmon IDS Probe powered by Suricata and allows the system to cover more attack vectors by combining the best of the two signature-less and signature-based approaches.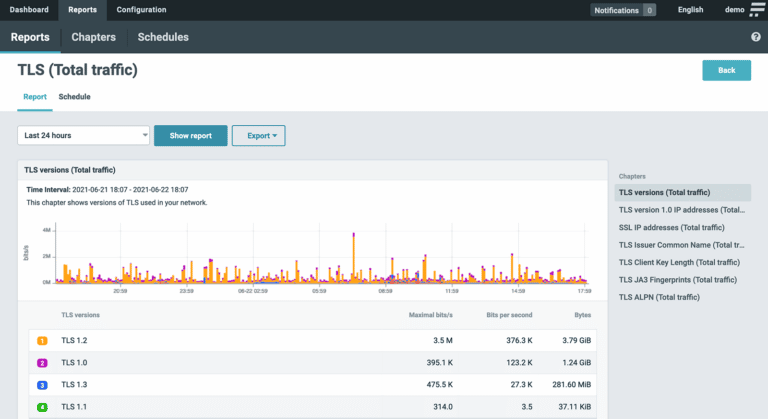
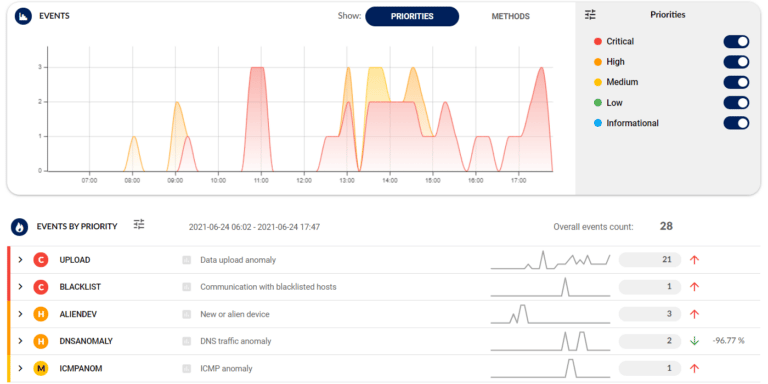
Minimize false positives and stay focused
Center on relevant issues only. The ADS distinguishes between anomalies and normal traffic and only alerts you when a real danger occurs. Detected security events are ranked by severity, and the solution’s built-in expertise enhances your situational awareness and speeds up triage and response.Detection and response explained
1. Detection
Machine learning, adaptive baselining, heuristics, behavior patterns, reputation databases, signature-based detection – all combined into one versatile capability that examines network traffic from multiple points of view and thus covers a wider spectrum of scenarios.
2. Reporting
The analytical view provides context-rich visualization of every attack including MITRE ATT&CK® mapping with drill-down analysis for a detailed understanding of what exactly is happening.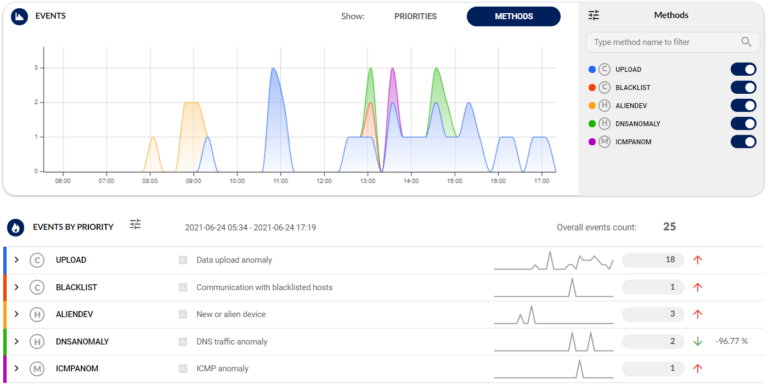
3. Triage
Incidents are ranked according to your priorities with an easy-to-use customization wizard that builds upon battle-tested, out-of-the-box configuration.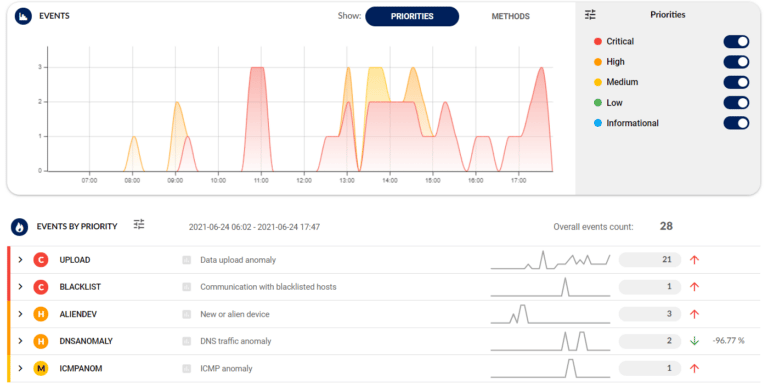
4. Response
Flowmon ADS can be integrated with network access control, authentication, firewall or other tools for immediate and automated incident response.
Integrations
Flowmon serves as a critical source of information to log management, SIEM, big data platforms, incident handling or response tools. You may integrate it via syslog, SNMP, email, REST API or custom scripts.Network telemetry
Logging and reporting
Feed your log management or SIEM system with comprehensive logging with context-rich syslog or SNMP messages. Maximize visibility across the IT environment or log events into your ticketing tools automatically.


